Tailscale is Awesome

I have heard of VPN for a very long time since I was still an undergrad. Despite the theoretical stuff that your professor taught you (and made you recite), many of us also have heard of it being a great tool to, well, you know, surf on the part of the Internet where you "should not be able to see" at all.
I have never thought that VPN can be that simple to use, or even host one yourself, until I get to know Tailscale.

Basically, once you sign up for an account, you can just enroll your devices of supported types (which is almost every kind of platforms out there), and you will have your devices connected with each other with LAN IPs.
It is built on top of WireGuard (which is probably the most popular VPN protocol now) and a bunch of other technologies.
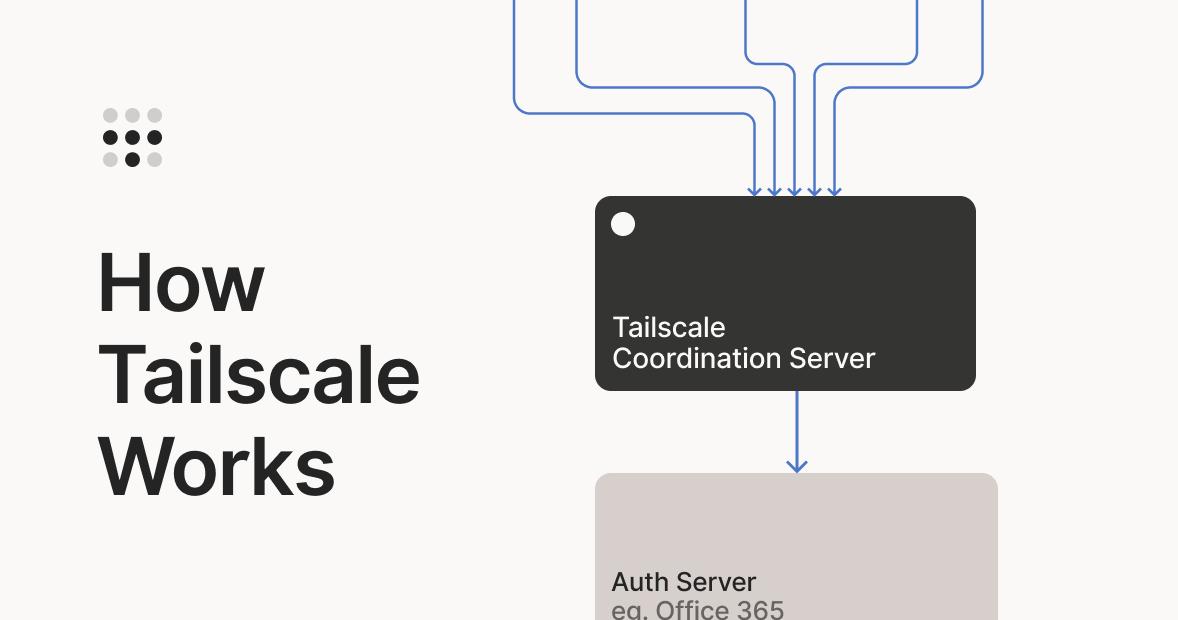
For those of people who are in favor of self-hosting everything, here is some good news. There is an open-source version of the coordination server, which is at the central of a Tailscale network. It is almost a drop-in replacement of Tailscale's official one which means you can easily self-host your own coordination server, and have the proprietary clients still work with it seamlessly. This is Headscale.
I personally use Headscale so that I can have full control of my own network. Comparing to Tailscale, it surely misses some functionalities, including a nice Web UI (although you can also find open-source ones) and some more premium features. However, the features included in Headscale already fit my needs.
I use it hide some of my services that I don't want to expose to the Internet at all. For example, I self-host my own grammar checker:
If you host it publically, you risk your resource being exploited by others without you noticing. As long as someone finds out about the URL of your checker, they can just use it in their own clients, as the clients provided by languagetool-org do not come with any authentication mechanism you can use out-of-box.
It's also worth noting that, comparing to vanilla WireGuard, despite the ease of setup and usage, Tailscale and Headscale also make setting any of your nodes to be an exit node much easier.
It will re-route all the network traffic through your designated exit node, so that you will be like just right next to your exit node physically.
MagicDNS is also a feature that you shouldn't miss. Basically, it works like your own DNS server inside your network, so that you don't have to remember the host and the port number of each of your services. Just name them with some easy to remember domain names.
You can either use Let's Encrypt, or make use of Coolify's (which we talked about in Journey of Self-Hosting (4): Coolify) feature of taking care of certificates for your automatically, to set up HTTPS for your MagicDNS domain names.
